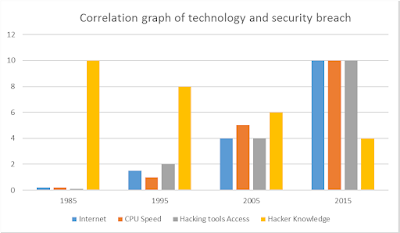
Cyberspace (internet, work environment, intranet) is becoming a dangerous place for all Organizations and individuals to protect their sensitive data or reputation. This is because of the numerous people and machines accessing it. It is important to mention that the recent studies have shown a big danger is coming from internal threats or from disappointed employees like the Edward Snowden case, another internal threat is that information material can be easy accessible over the internet.
Potential Losses Due to Cyber Attacks:
The potential loses in this cyberspace are many even if you
are using a single computer in your room. Here, I will be listing some examples
that have a direct impact on you and on others:
1. Losing your data :- If your computer has been hacked or infected, there is a big chance that all your stored data might be taken by the attacker.
2. Bad usage of computer resources :- This means that your network or computer can go in overload so you cannot access your genuine services or in a worst case scenario, it can be used by the hacker to attack another machine or network.
3. Reputation Loss :- Just think if your Facebook account or business email has been owned by a social engineering attack and it sends fake information to your friends, business partners. You will need time to gain back your reputation.
4. Identity Theft :- This is a case where your identity is stolen (photo, name surname, address, and credit card) and can be used for a crime like making false identity documents.
. . .
Basic Computer Security Checklist
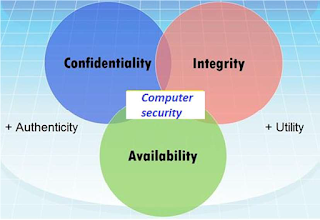
Different elements in Cyber Security
Confidentiality
Confidentiality is the concealment of information or
resources. Also, there is a need to keep information secret from other third
parties that want to have access to it, so just the right people can access it.
Example in real life: Let’s say
there are two people communicating via an encrypted email they know the
decryption keys of each other and they read the email by entering these keys
into the email program. If someone else can read these decryption keys when they
are entered into the program, then the confidentiality of that email is
compromised.
Integrity
Integrity is the trustworthiness of data in the systems or resources
by the point of view of preventing unauthorized and improper changes.
Generally, Integrity is composed of two sub-elements – data-integrity, which it
has to do with the content of the data and authentication which has to do with
the origin of the data as such information has values only if it is correct.
Example in real life: Let’s say you are doing an online payment of 5 USD, but your information is tampered without your knowledge in a way by sending to the seller 500 USD, this would cost you too much.
In this case cryptography plays a very major role in
ensuring data integrity. Commonly used methods to protect data integrity
includes hashing the data you receive and comparing it with the hash of the
original message. However, this means that the hash of the original data must
be provided in a secure way.
Availability
Availability refers to the ability to access data of a
resource when it is needed, as such the information has value only if the
authorized people can access at right time. Denying access to data nowadays has
become a common attack. Imagine a downtime of a live server how costly it can
be.
Example in real life: Let’s say a
hacker has compromised a webserver of a bank and put it down. You as an
authenticated user want to do an e-banking transfer but it is impossible to
access it, the undone transfer is a money lost for the bank.
. . .
Guidelines for Windows OS Security
Following are the list of guidelines for Windows Operating
System Security.
1. Use the licensed versions of Windows OS, not the cracked or
pirated ones and activate them in order to take genuine updates.
2. Disable Unused Users: To do this,
Right Click on Computer – Manage – Local Users and Groups – Users, then disable
those users that are not required. In my case, I disabled the Guest and
Administrator users and I created a new non-default like Admin.
3. Disable unused shares: By default, Windows OS creates shares, please see the following screenshot. You have to disable them and to do this, you follow:
Right Click on My Computer – Manage – Shared Folders – Right Click Stop Sharing.
4. The next step is to take updates regularly for Windows OS. It is recommended to do them automatically and periodically. To set this up, go to Control Panel – System and Security – Windows Updates –OK.
5. Put your Windows System Firewall up, this will block all the unauthorized services that make traffic. To set this up, go to Control Panel – System and Security –Windows Firewall.
. . .
What is Virus?
After finding this file, I opened it with a text editor and as thought the text was not Understandable as shown in the following screenshot on the next image.
After finding this, I tried it on a base64
decoder and I found that it was a Virus file.
This virus can cause the following to your computer:
1. It may delete important data from your computer to gain space for their processes.
2. It may avoid detection by redirection of disk data.
3. may perform tasks by triggering an event with itself. For example, this happens when in an infected computer pop-up tables etc., show up automatically on the screen.
4. They are common in Windows and Mac OS because these operation systems do not have multiple file permissions and are more spread out.
. . .
References:
1.
Jump
up^ Bell, David
J. et al, eds. (2004). "Virus". Cyberculture: The Key Concepts. Routledge.
p. 154. ISBN 9780203647059.
2. Jump up^ Stallings,
William (2012). Computer security : principles and practice. Boston:
Pearson. p. 182. ISBN 978-0-13-277506-9
https://www.base64encode.org/enc/virus
www.quantenblog.net/security/virus-scanner-bypass
https://www.wikihow.com/Create-a-Fake-and-Harmless-Virus
https://www.youtube.com/watch?v=vkxtOr2RLbY
C











Comments
Post a Comment